Inside the SOC: The 6 Phases that Keep Your Business Secure
In today’s digital-first world, cyber risk is no longer something that concerns only large enterprises or tech heavy companies.
The truth is simple: no organization is too small, too niche, or too early-stage to be targeted. Attackers today operate at scale, using automation and AI to exploit from misconfigured cloud workloads, exposed employee credentials, to overlooked SaaS permissions making every organization a potential entry point.
Businesses today are growing at a pace we’ve never seen before. Teams are picking up new SaaS tools frequently, workloads are spreading across multiple clouds, and remote or distributed workforces have become the norm. All of this is great for innovation but it also opens up a much bigger attack surface.
For Security Operations Center (SOC), this introduces a pressing challenge: How do you spot, investigate, and stop threats quickly when your digital landscape keeps expanding?
The answer lies in adopting a structured, well-governed SOC lifecycle which helps organizations implement, scale, and modernize with precision.
Why the SOC Lifecycle Matters and Where Companies Struggle?
Most organizations aren’t struggling because they lack tools, they’re struggling because the tools don’t talk to each other, processes aren’t standardized, or analysts are overwhelmed by noise instead of insights.
A well-defined SOC lifecycle brings order, consistency, and confidence across six critical stages:
Detection
Alerting
Investigation
Containment
Eradication and Recovery
Post-Incident Review
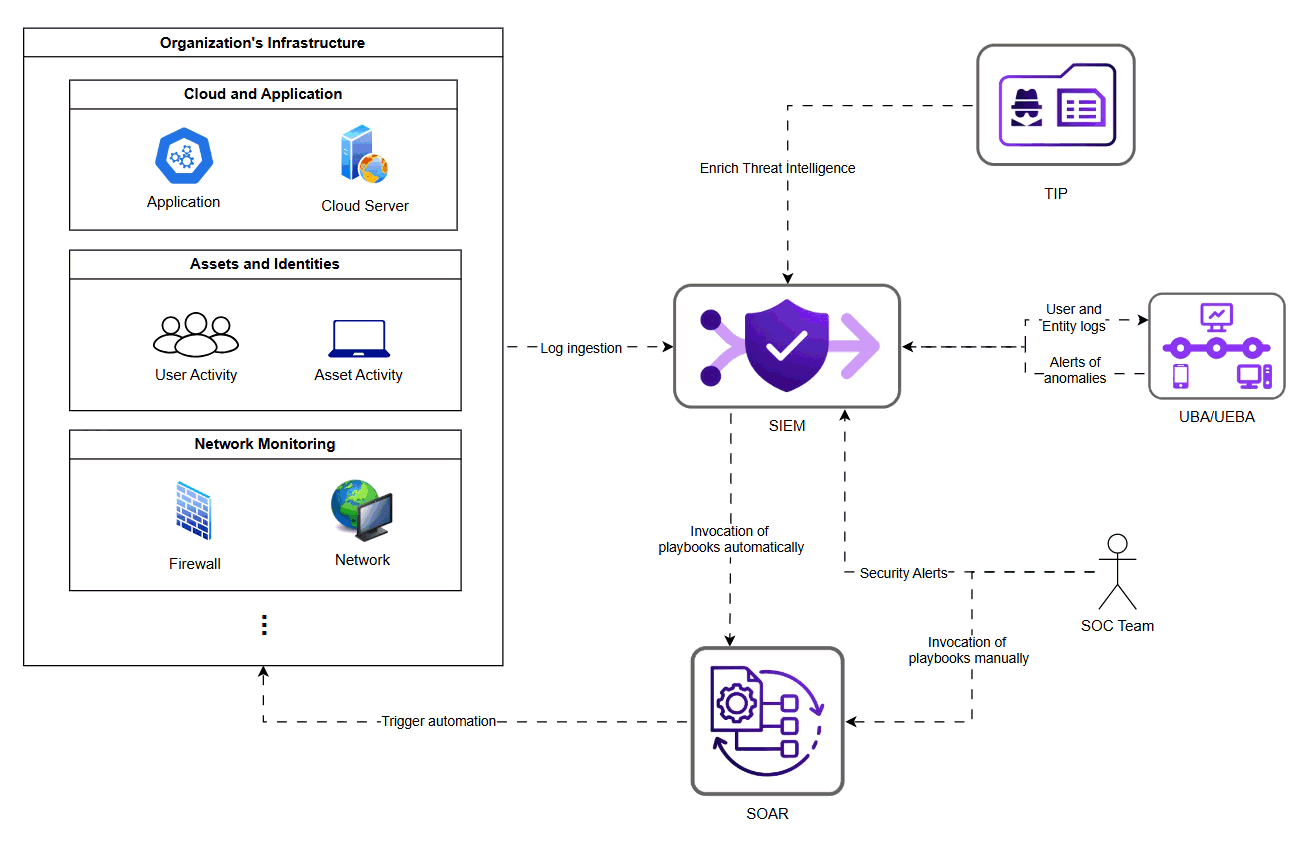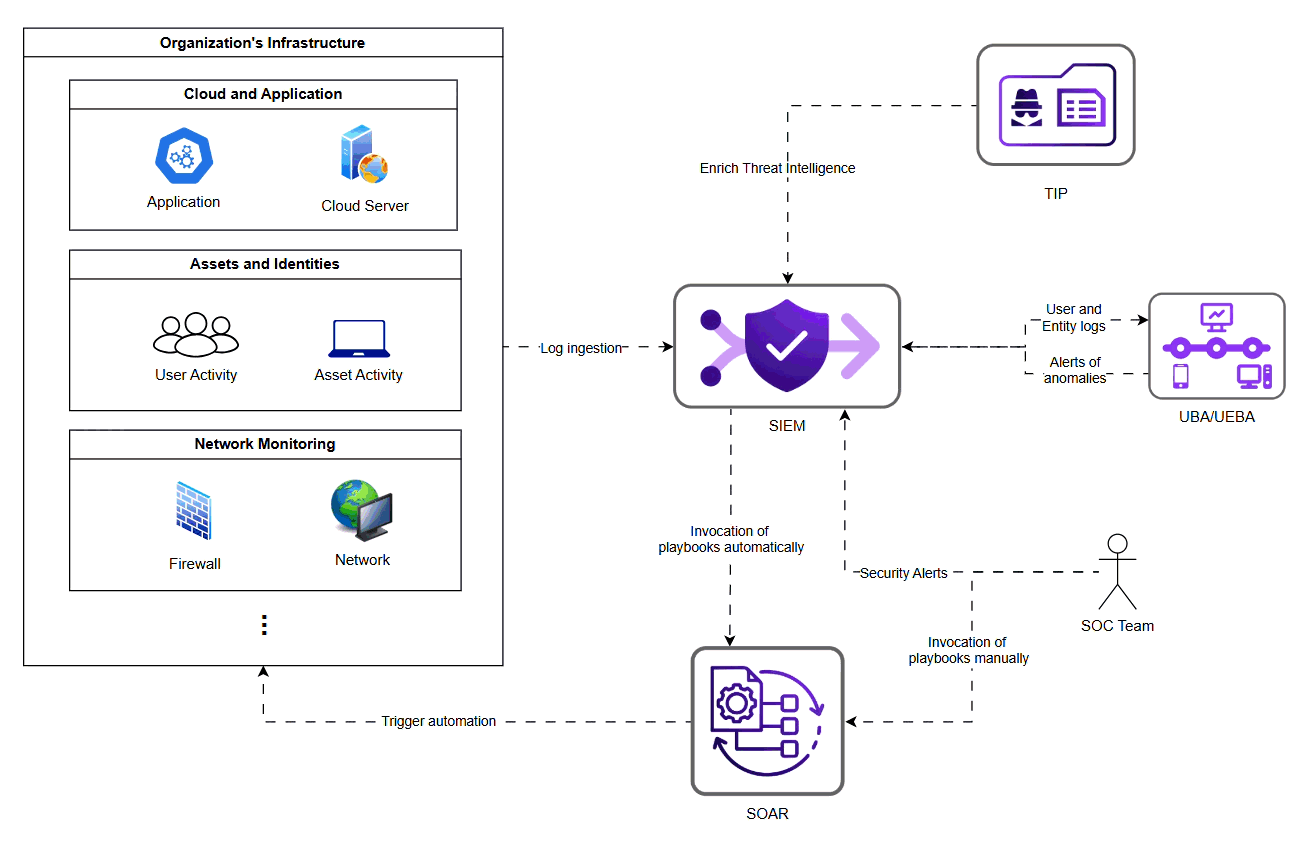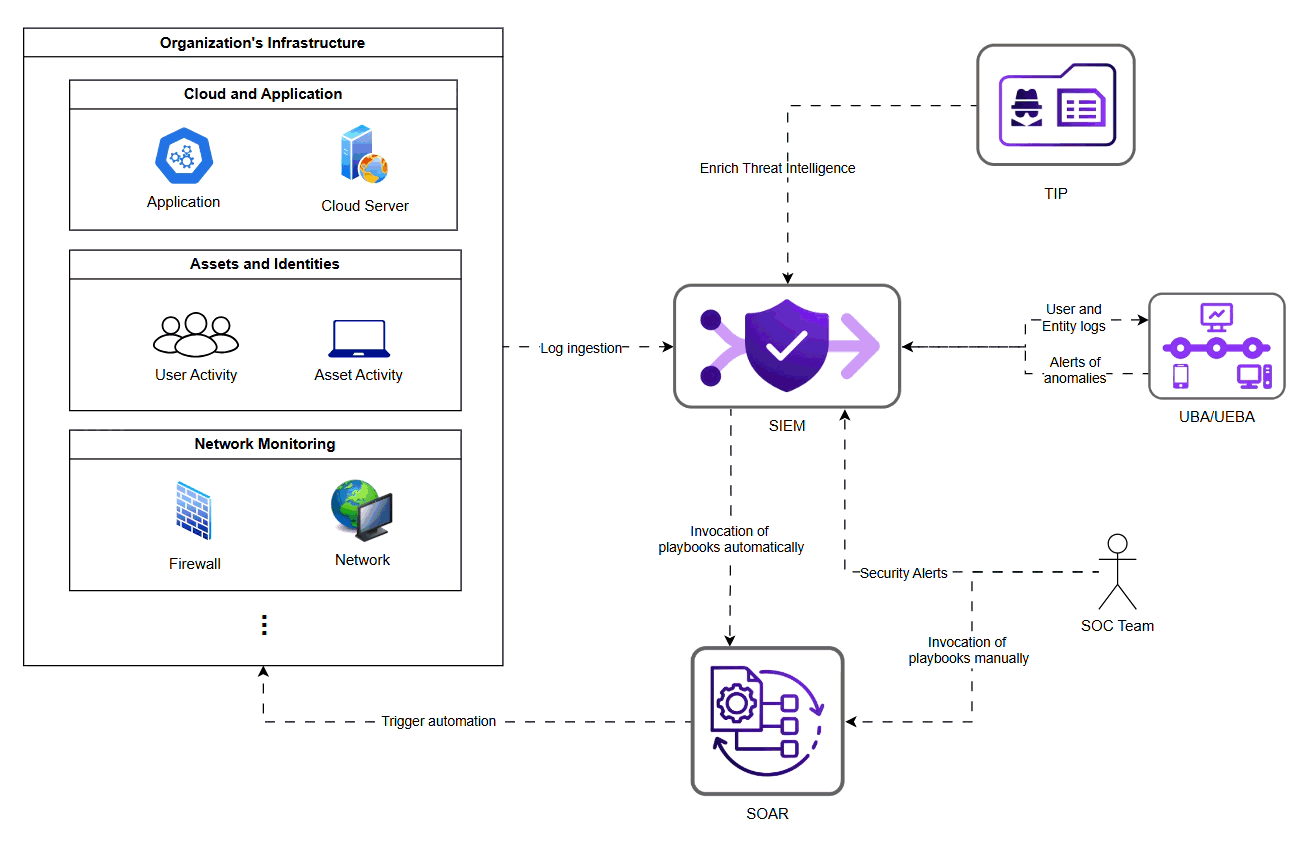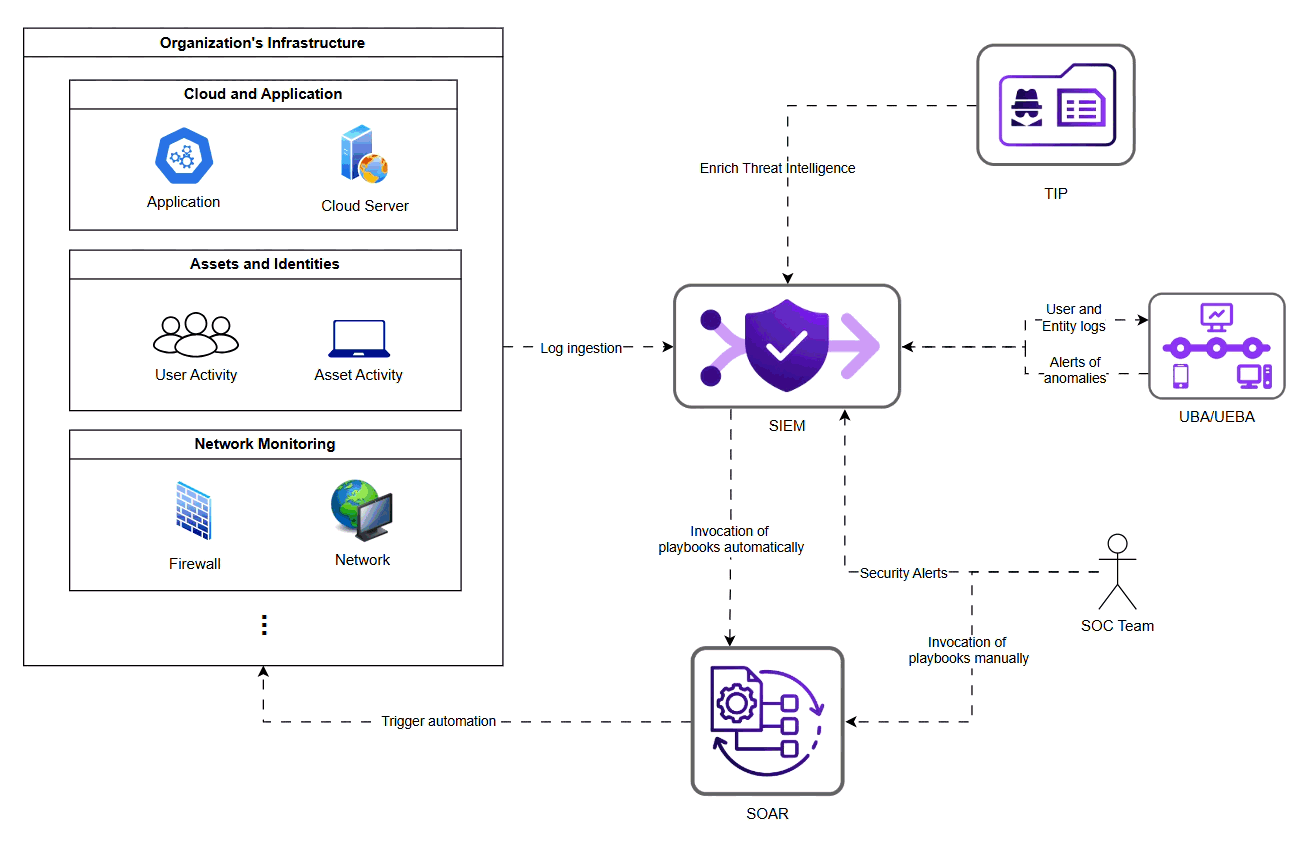
How Modern SOC Tools Work Together to Maximize Value
Modern SOC rely on a combination of tools:
SIEM Aggregates logs and performs correlation to generate alerts.
SOAR Automates investigation and response steps.
UBA/UEBA Surfaces behavioural deviations and potential insider threats.
Threat Intelligence Platform (TIP) Adds context about known Indicator of Compromise (IoCs) and adversaries.
Individually these tools are powerful, but their true strength is unlocked only when they are integrated into a cohesive lifecycle. When implemented and optimised effectively, they enable organizations to achieve: cleaner detection signals, reduced false positives, automated triage, faster containment, consistent, repeatable workflows, intelligence-driven improvements.
This leads to a stronger security posture and better utilisation of internal analyst time, something every modern business needs.
Security Alert Lifecycle Flow
Ways Strong SOC Processes Strengthen Enterprises Security
1. Faster, Smarter Detection
When SIEM insights, UEBA behaviour patterns, and threat intelligence work together, organizations gain true visibility across their entire digital environment. Unusual logins, suspicious cloud actions, abnormal users and more, behaviour are spotted earlier often before they escalate into real damage.
2. High-Quality, Low-Noise Alerting
With enriched alerts and SOAR-powered routing, teams deal with fewer distractions and far less fatigue. Analysts receive only the alerts that matter, helping them stay focused, efficient, and ready for genuine threats not buried under noise.
3. Investigations that Actually Flow
Bringing logs, behaviour analytics, and threat intel into one unified picture makes investigations smoother and far less chaotic. Automated enrichment cuts down manual steps, giving analysts the clarity they need to make faster, more confident decisions.
4. Rapid, Automated Containment
When something does go wrong, automation becomes a game-changer. With SOAR, actions like disabling compromised accounts, blocking malicious IPs, or revoking risky permissions can happen instantly, reducing the blast radius within seconds and protecting the business from further harm.
5. Confident Eradication and Smooth Recovery
Once the threat is understood, SIEM visibility and SOAR-driven actions help teams to fully remove malicious artefacts, fix vulnerabilities, restore systems, and validate that everything is clean before operations resume. This ensures recovery is safe, controlled, and complete.
6. Continuous Learning that Makes the SOC Smarter Over Time
Post-incident insights whether from dashboards, SOAR playbook data, or behavioural trends help organizations continually improve. Detection rules get sharper, workflows get faster, and automation expands naturally based on real-world lessons.
The Outcome?
A mature, predictable, and resilient security operation that stays ahead of modern attackers.
The Bottom Line: Stronger SOC Start with Stronger Partners
The cyber landscape isn’t easing up. Threats are more automated, more adaptive, and more relentless than ever. But with a well-defined SOC lifecycle and the right partner to operationalize it, organizations can stay secure, scalable, and resilient.
Crest Data - The Strategic Partner for Modern Businesses
In a threat landscape where cyberattacks are faster, smarter, and more relentless, organizations need more than tools; they need a partner who can help them scale security with precision. Crest Data, a data and AI-first product engineering and technology solutions provider, is trusted by over 150 global enterprises for its deep expertise across Agentic/GenAI, Cybersecurity, Observability, Data Analytics, Workflow Automation, and Cloud.
Crest Data brings the perfect blend of advanced tooling and human expertise, ensuring your SOC evolves as fast as the threats targeting your business.
For businesses looking to strengthen their SOC maturity, modernize ecosystems, or build intelligent, secure, and future-ready operations, Crest Data offers a unified approach that connects data, automation, and AI to create measurable impact. As cyber threats continue to evolve, partnering with Crest Data enables businesses to operate with confidence, resilience, and speed.